![[background image] image of office space (for a trucking company)](https://cdn.prod.website-files.com/image-generation-assets/bed170d3-04a7-492d-9440-aae64732fb6b.avif)


.png)
Adopting ML-KEM is a step forward, but relying on a single algorithm is not a strategy. This blog explains why mono-algorithm approaches increase systemic risk, how real-world deployments demand cryptographic diversity and agility, and what a resilient post-quantum strategy should look like beyond compliance checkboxes.
Cryptography isn’t just algorithms on paper. It lives across APIs, applications, hardware, vendors, and cloud layers. This blog breaks down where cryptography actually resides inside modern enterprises, why that visibility gap creates serious post-quantum risk, and how organisations can regain control before migration becomes chaos.
Everyone talks about speed in cybersecurity, but few confront how slow cryptographic change really is. This blog examines the growing gap between AI-driven attacks and enterprise crypto migrations, and why that mismatch is becoming a structural risk. In a world where attackers adapt in minutes, taking years to change encryption is no longer a technical issue, it is a security failure.

Monroe, La. USA & Melbourne, Australia - Dec 12, 2025 - In a significant advancement for global cybersecurity and digital trust, identity-security provider Krown Technology and quantum-safe security company ExeQuantum today announced a jointly engineered patent for Signature Factor Authentication (SiFA), a new category of cryptographic, automated multifactor authentication designed to prevent fraud before it occurs.

The true cost of PQC isn’t in adopting early - it’s in waiting until quantum risk forces an emergency, where retrofitting becomes exponentially more expensive and disruptive. Organisations that delay face premium consulting rates, outages, compliance penalties, and heightened exposure to harvest-now-decrypt-later attacks. Proactive migration creates predictable, controlled transformation instead of crisis-driven remediation.
Everyone wants PQC explained in simple terms, but the truth is, oversimplification is exactly what keeps organisations unprepared. This blog breaks down why quantum readiness requires nuance, awareness, and an honest confrontation with the scale of the challenge. Because in 2025, “I don’t understand PQC” isn’t harmless, it’s a risk signal.

ExeQuantum has now moved from early pilots into a full-scale quantum-safe rollout across multiple sectors. Following a successful pilot program with early adopters, our platform is being deployed to secure long-life data, supply-chain systems, and high-assurance workflows using standards-aligned hybrid PQC.

Last week, ExeQuantum convened a group of Australia’s leading CISOs, technologists, and cybersecurity executives for a frank discussion about one of the most urgent security challenges of our time: quantum readiness.

ExeQuantum was selected to speak at the PQC Summit Kuala Lumpur 2025, hosted by the PKI Consortium, where Founder and CEO Samuel Tseitkin contributed to the roundtable “Securing the Healthcare Sector in the Quantum Era.”

The Australian Trade and Investment Commission (Austrade), together with Quantum Australia, has published the Australian Quantum Technology Industry Capability Report (September 2025). This government-backed report highlights Australia’s leadership in quantum technologies and showcases companies that are ready to deliver globally competitive solutions.
ExeQuantum, a rising leader in post-quantum cryptography (PQC) and secure digital infrastructure, today announced the appointment of Audrey Nicoll as Chief Marketing & Growth Officer (CMGO).

The cryptographic community is entering a new phase. With NIST finalising post-quantum cryptography (PQC) standards such as ML-KEM and ML-DSA, the big question is no longer which algorithms to adopt, but how to implement them in ways that are fast, trustworthy, and ready for deployment at scale.

For decades, cryptography has been the invisible glue of our digital world, securing payments, protecting communications, and underpinning the trust that makes the internet possible. But in a world of rising geopolitical tension and technological disruption, two competing imperatives are colliding: cryptographic sovereignty and global standardization.

ExeQuantum, a global leader in post-quantum cryptography (PQC) solutions, is proud to announce a strategic partnership with Malaysian firm Notable Frontier to spearhead the growth of quantum-resilient technologies across Southeast Asia.

Earlier this year, ExeQuantum published the STAC doctrine, a framework for security infrastructure built on Sovereignty, Transparency, Agility, and Compliance.The response was clear: people resonated with the values. But they also had a question.“How do you implement STAC?”

ExeQuantum is proud to announce the expansion of our leadership and cryptographic research team as we accelerate our mission to build quantum-safe cybersecurity infrastructure.

How ExeQuantum Helps You Modernize Without Giving Up Control.

As the global cybersecurity community races to adopt quantum-safe standards, the real challenge is no longer just algorithm selection, it’s deployment. Cryptography doesn’t live in white papers; it lives in code, in infrastructure, and increasingly, in hardware.

ExeQuantum, an Australia-based leader in post-quantum cryptographic infrastructure, and Krown Technologies, a leading US-based quantum blockchain, crypto, and DeFi ecosystem developer, today announced a strategic partnership focused on advancing global cryptographic diversity and long-term blockchain resilience.

In an age where cloud providers are global, attack surfaces are sprawling, and quantum threats are no longer theoretical, one principle is rapidly becoming non-negotiable: cryptographic sovereignty.

ExeQuantum and CyberWaze unite to deliver post-quantum encryption to the Middle East, supporting Saudi Arabia's Vision 2030 and broader critical sector resilience

At ExeQuantum, we don’t see HSMs (Hardware Security Modules) as a competitor or replacement. In fact, we see them as crucial, but unoptimised. HSMs are exceptional at secure key storage and tamper resistance. But when it comes to agility, quantum readiness, and computational efficiency, they start to show cracks.

On March 4th, a research team led by Professor Jintai Ding at Xi’an Jiaotong-Liverpool University (XJTLU) set a new world record by solving a 200-dimensional instance of the Shortest Vector Problem (SVP). This breakthrough in the International Open Darmstadt SVP Challenge, achieved entirely with classical computing resources, has reignited global discussion around the robustness of lattice-based cryptography and the future of post-quantum security.

In the race to prepare for quantum computing, the cryptographic community has made monumental progress. Breakthroughs in lattice- and code-based cryptography have culminated in new standards, rigorous academic vetting, and the formalization of post-quantum cryptographic (PQC) algorithms like ML-KEM and ML-DSA.
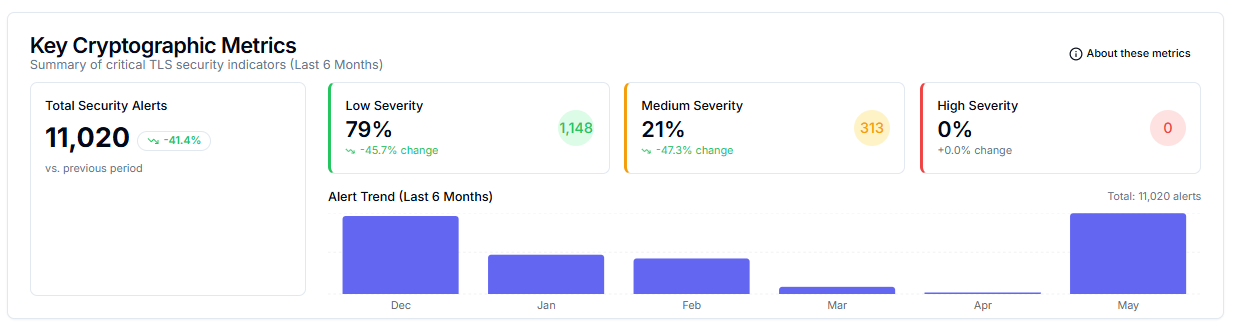
QryptoCyber, a pioneer in cryptographic discovery and inventory, has joined forces with ExeQuantum, a leader in post-quantum cryptography solutions, to launch the world’s first end-to-end cryptographic remediation platform. This strategic partnership delivers a unified solution covering everything from comprehensive cryptographic inventory to push-button remediation of select cryptographic protocols.

As quantum computing continues its rapid ascent, so too does the urgency to secure our digital infrastructure against it. Amid the noise, two technologies dominate the conversation: Post-Quantum Cryptography (PQC) and Quantum Key Distribution (QKD).

As quantum computing progresses from theory to applied engineering, its threat to classical encryption is no longer a distant horizon, but a growing concern for CIOs, CISOs, boardrooms, regulators and policymakers.

At ExeQuantum, we believe post-quantum cryptography (PQC) isn’t just a research milestone, it’s a deployment challenge. And we’re solving it.We’ve taken one of the most advanced post-quantum algorithms, HQC-192, and made it accessible via API, deployable in production, and usable today, not someday.

Quantum computing is evolving rapidly, bringing unprecedented opportunities — and equally profound security challenges. While blockchain technology is often praised for its decentralisation and security, it remains vulnerable to emerging quantum threats that could undermine its cryptographic foundations.

In cybersecurity, crypto agility has emerged as a buzzword — particularly in conversations around post-quantum cryptography (PQC). It is positioned as a critical capability, allowing organisations to seamlessly adapt cryptographic systems in response to new threats. In theory, it sounds like an elegant and forward-thinking approach.

In today’s digital landscape, the stakes for data privacy and security have never been higher. With cyber threats rapidly evolving and the future of quantum computing approaching, the need for advanced cryptographic solutions is paramount. Enter ExeQuantum and SharePass: two companies committed to empowering users and enterprises alike with cutting-edge technologies to safeguard sensitive data.
Quantum computers are poised to outperform classical computers by an exponential margin. While this presents numerous opportunities, it also means that traditional encryption methods will no longer be secure.