Automatically map every cryptographic asset across your estate, be it algorithms, key lengths, libraries, certificates, and endpoints. Identify legacy and risky usage, flag weak configurations, and generate migration plans to quantum‑safe standards with clear, action‑ready reports.
Cryptographic discovery is the first step in your quantum migration.
Visibility
Know what you have
Inventory all cryptographic assets
Identify algorithms and key strengths
Map usage across applications and devices
Spot outdated or weak cryptography
Risk Awareness
Understand your exposure
Detect algorithms at risk from quantum attacks
Identify non-compliant encryption usage
Highlight systems without crypto agility
Prioritize assets based on sensitivity
Action Readiness
Be ready to respond
Develop a migration roadmap
Simulate post-quantum upgrade paths
Integrate continuous cryptographic monitoring
Align with compliance and sovereignty mandates
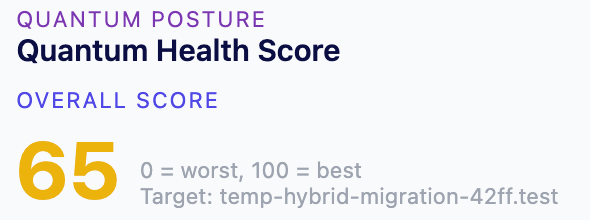
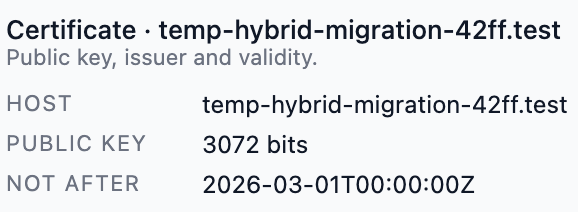
- Inventory, expiry, chain validity, weak signature algorithms, key sizes
- Where certificates are used (endpoint mapping)
- JWT/Auth posture
- Libraries/frameworks
- Algorithms, modes, hardcoded keys
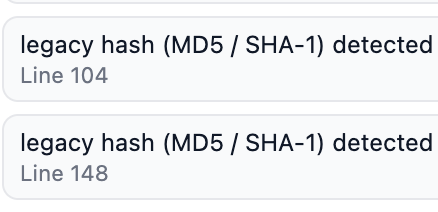
- Hashes and general vulnrabilities
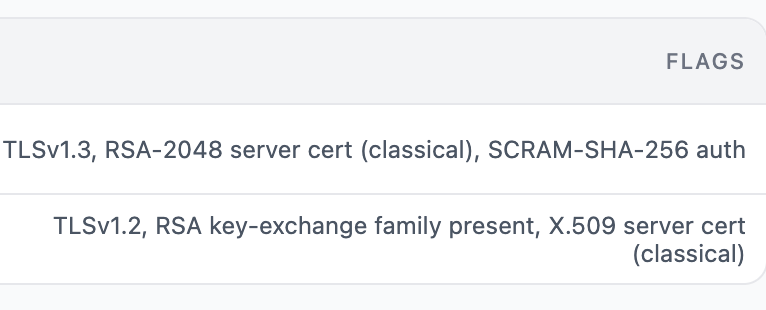
- DB encryption config (TDE etc)
- backups encryption posture
Quantum computing is coming faster than most organizations expect. “Harvest Now, Decrypt Later” attacks are already happening, and regulators worldwide are setting deadlines for post-quantum cryptography adoption.



Identify every cryptographic asset across your infrastructure, including algorithms, keys, certificates, and protocols.
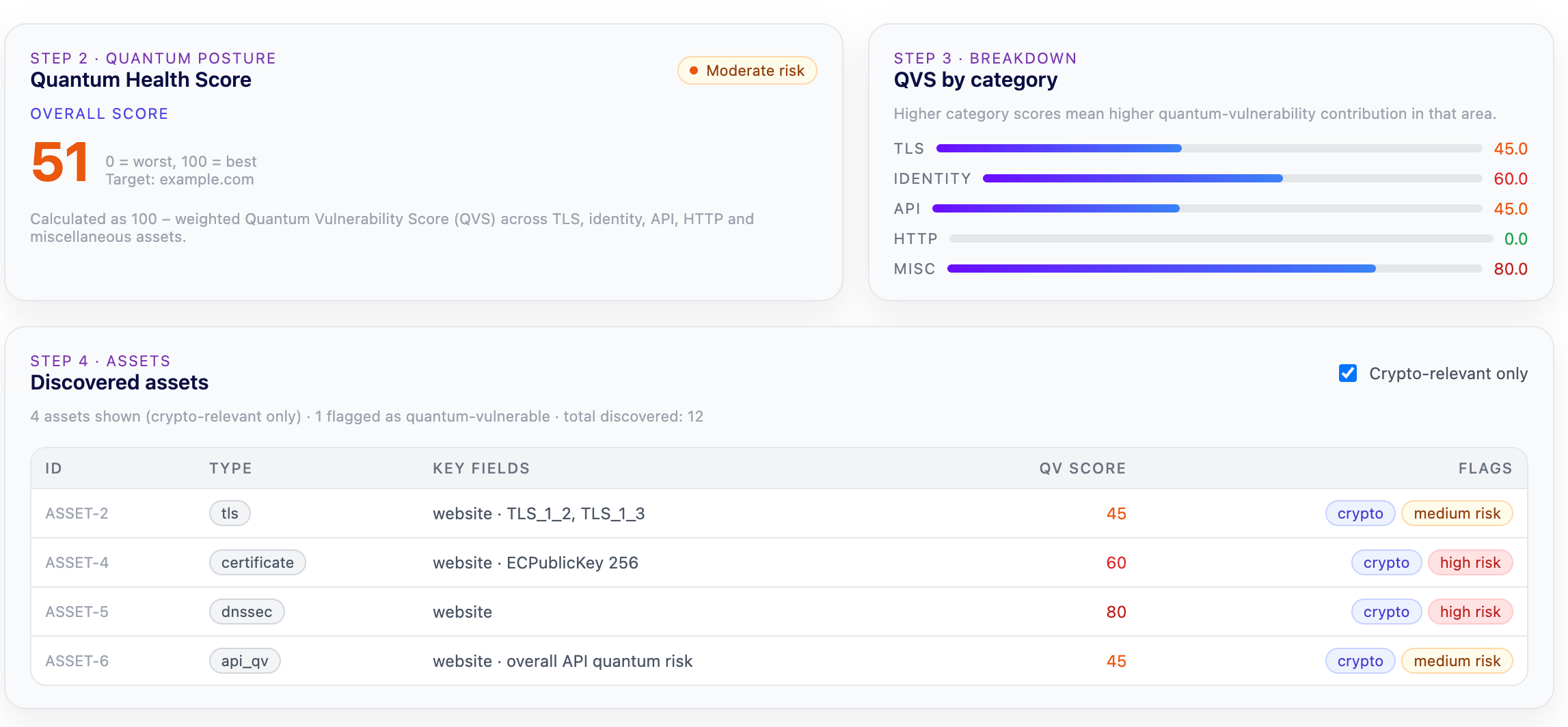
Classify assets by quantum vulnerability and measure post-quantum readiness with clear, actionable scoring.
Pinpoint where upgrades to quantum-safe cryptography can be applied with minimal disruption.

Automatically compare your crypto posture against global regulatory and industry standards (ISO, PCI DSS, GDPR, etc).

the API adapts to any environment, enabling rapid deployment and smooth interoperability with minimal friction.
Assists with mapping crypto use to asset criticality and migration playbooks. Disabled by default and fully on-premise.
Future-proof your data with post-quantum cryptography. Explore robust, compliant solutions for critical infrastructure.