
Attackers are already stealing encrypted data today (“harvest now, decrypt later”). Sensitive data like health, identity and financial records remain valuable for decades. If we don’t migrate early, that data is at risk the moment quantum capability arrives.
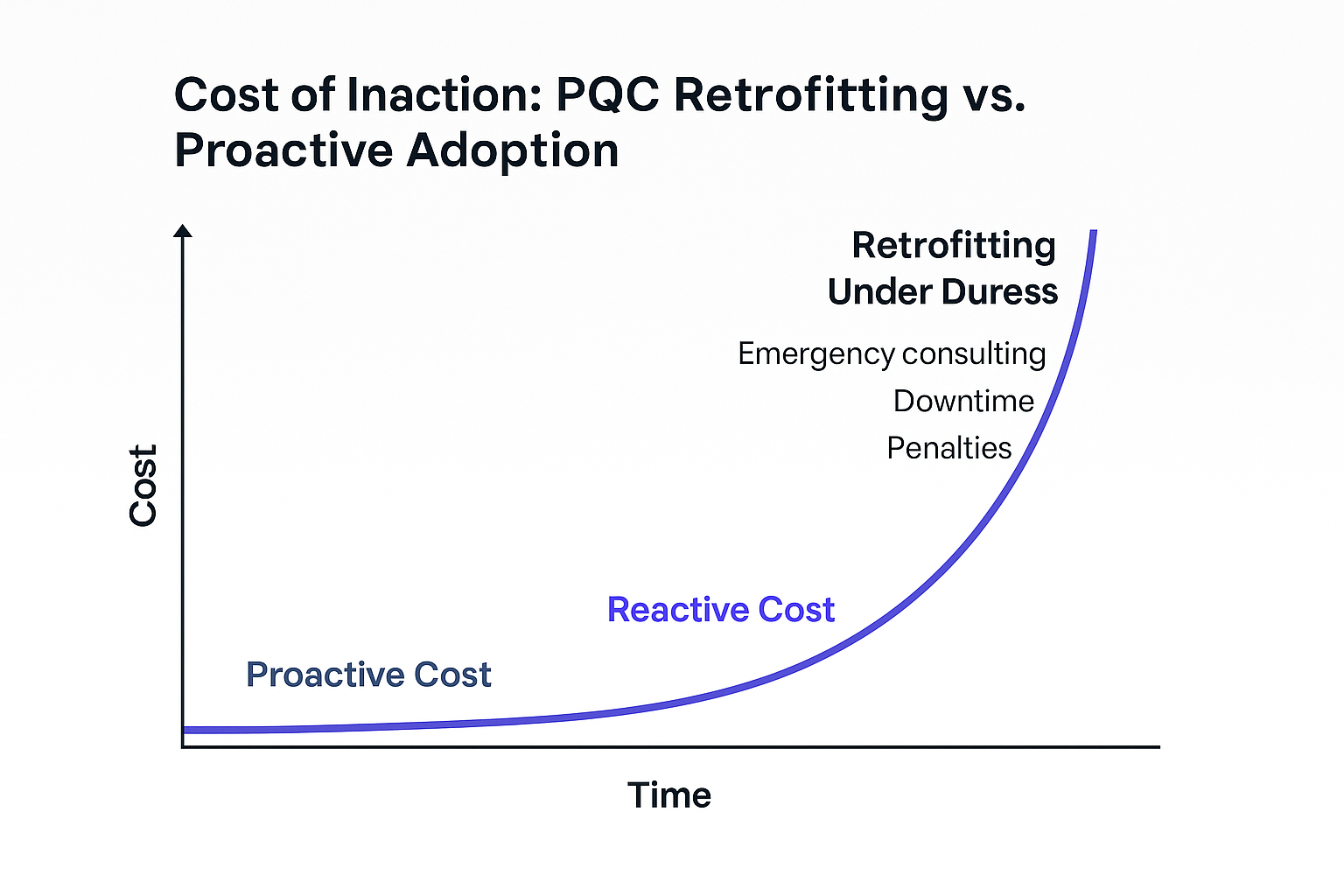
NIST has already standardised core PQC algorithms (ML-KEM, ML-DSA, SLH-DSA). Waiting means you will be forced into an emergency migration, competing with every other enterprise and vendor for the same scarce expertise.
Inaction exposes you to:
- Breach liability of $50M-$150M+ (based on Optus/Medibank precedents).
- OAIC/APRA non-compliance fines of up to $50M.
- Loss of customer trust and market share.
- Higher insurance premiums and possible loss of cover.
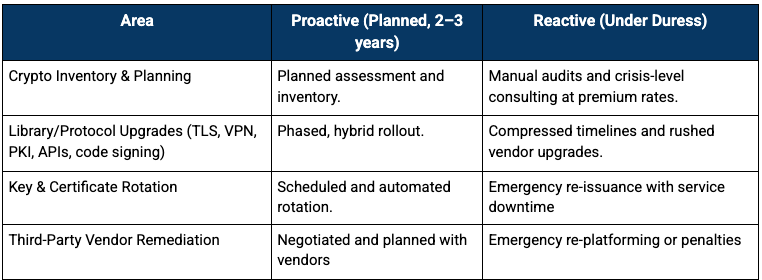
- Complete crypto inventory (you may not know where all RSA/ECC is used).
- Hybrid TLS and PQC pilots; demonstrating customer-facing leadership.
- Crypto-agile infrastructure that reduces lock-in and improves overall cyber maturity.
- Third-party supplier uplift clauses; closing one of our biggest breach vectors.
Early movers can market PQC readiness as a trust differentiator, particularly in financial services, healthcare, and critical infrastructure. Customers and regulators will favour organisations that are demonstrably “future-proof.”