Quantum-Powered Entropy for Cryptographic Assurance
Enhance key generation integrity using true quantum randomness. Verified, sovereign, and audit-ready.
Designed for enterprise, national identity platforms, regulated financial infrastructures, and critical deployments.

Why Quantum-Powered Entropy Matters
Classical pseudo-randomness, while mathematically complex, remains algorithmically derived. Enterprise-grade cryptographic assurance demands **provably unpredictable entropy**, minimizing risks from algorithmic weaknesses and AI-powered key modeling.

Provable Key Integrity
Quantum-generated entropy ensures that cryptographic key material remains unpredictable and non-reproducible, even under advanced adversarial analysis.

Client-Controlled Integration
Deployable across sovereign clouds, air-gapped facilities, or client-controlled private infrastructure. Fully auditable under national regulatory frameworks.
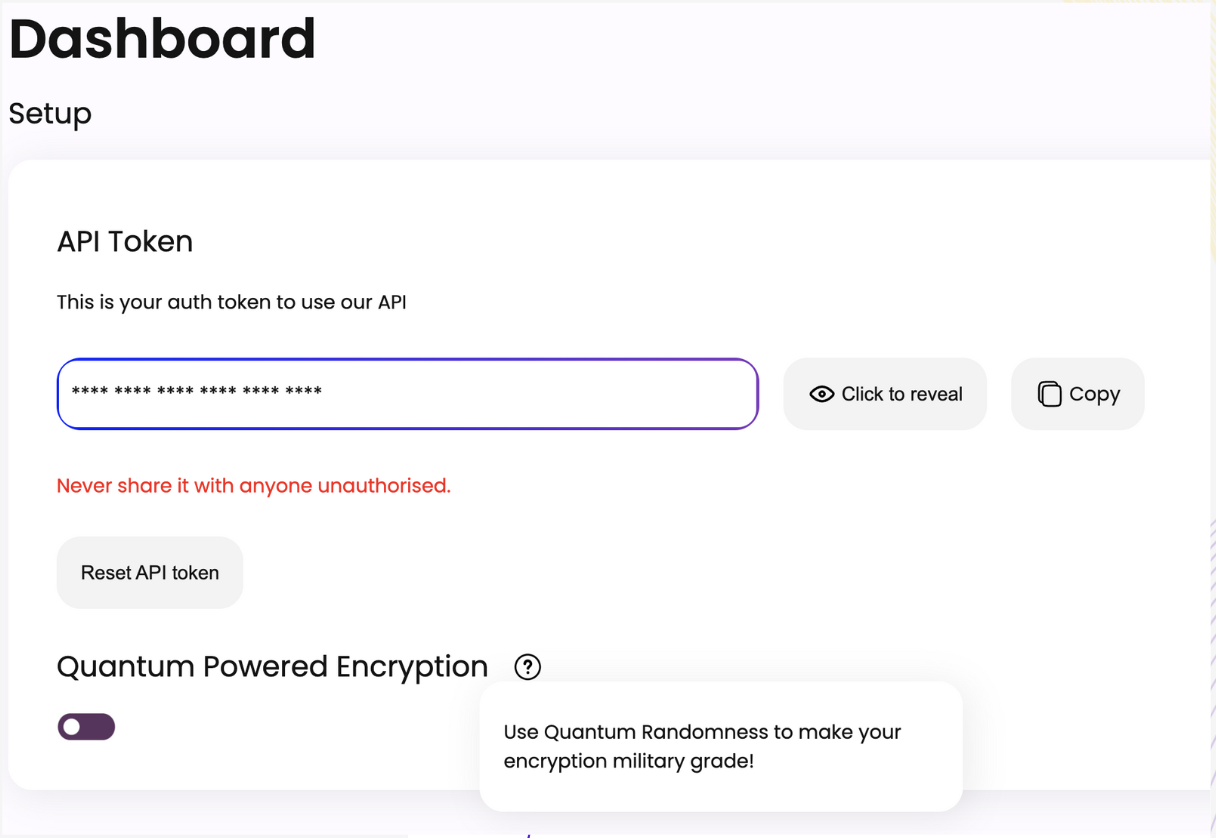
Auditable Entropy Supply Chain
All entropy operations are logged, verified, and subject to client-directed oversight — ensuring trust-by-transparency, not trust-by-vendor claim.
Quantum-Powered Modules You Control
Our entropy orchestration layer interfaces directly with QRNGs, while allowing oversight, physical isolation options, and regulatory alignment per deployment.
Note: Activation requires enterprise engagement. Please contact us to discuss local deployment options and jurisdictional compliance requirements.
Tailored Pricing Based on Deployment Models
Quantum entropy orchestration is priced based on deployment configuration, jurisdictional control, and volume of cryptographic key generation events. Formal pricing proposals are provided following private architectural assessment and regulatory review.
